Business as espionage or espionage as business?

We often hear statements that business is outside of politics. This justifies the activities of Russian offices in our country in a situation of direct confrontation between the Russian Federation and Ukraine. That would be half the trouble, but business often covers up espionage in favor of the aggressor country.
The aggression of Russia against Ukraine has been going on for the eighth year already. The world community and political leaders call this aggression a hybrid war. One of the features of such a war is the conduct of covert operations that undermine the security of our country from the inside. Such covert operations include a variety of sabotage, espionage, propaganda, cyber warfare and other methods. Subversive activities are often covered by business with the involvement of large international companies with significant authority. Moreover, such companies represent countries that, according to their official statements, support the independence and statehood of Ukraine, for example, the United States.
Let's look at one example of how this happens in practice, in order to do this, we don't even need to perform a deep journalistic investigation. It is enough to analyze the public available facts as the connection between them becomes obvious. So, the first fact: many manufacturers of IT equipment and software have not yet removed Russia from the chain of subordination of their representative offices in Ukraine to Russian offices. That is, the divisions of companies in Ukraine continue to directly report and report primarily to the office, usually located in Moscow. This subordination scheme within the structure of foreign companies and corporations is fraught with tremendous opportunities for Russia's significant influence on Ukraine and its critical infrastructure.
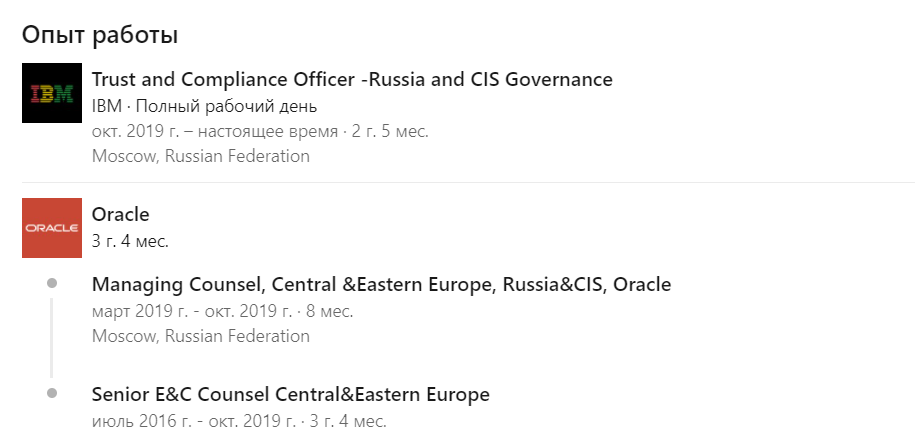
Fact two: a large American corporation - IBM, works according to this scheme. Currently, at IBM, the security and compliance division of the Ukrainian representative office is directly subordinate to the Russian office in Moscow. And now some data about specific persons: Olga Ivanchenko, citizen of Russia with an active civil position, an employee of IBM, a security officer of IBM (Trust and Compliance Officer - Russia and CIS Governance at IBM), in charge of Ukraine, Russia and the CIS countries, operates from an office in Moscow, Russia ... This information was obtained from partners who attended trainings that Ivanchenko personally conducted in Ukraine, as well as from social networks. Olga Ivanchenko was educated as a lawyer at the Russian Law Academy, where, as you know, cadres and agents for the FSB are forged and trained. Before joining IBM, she held similar positions at Oracle for a long time and also oversaw the work of the Ukrainian office.
The education and works records of O. Ivanchenko can be found on the screenshots below.

https://www.linkedin.com/in/ivanchenko-olga-7a94ab36/
Fact three: as a security officer at IBM, O. Ivanchenko has access to all placed orders for IBM products in the territory entrusted to her, including Ukraine. This includes both commercial customers and state-owned enterprises related to the critical infrastructure of Ukraine, such as: State Fiscal Service of Ukraine (SFS), National Bank of Ukraine (NBU), State Treasury Service of Ukraine, State Bureau of Investigation (GBR) "," Ukrainian State Center of Radio Frequencies (UHTSR)" and others. At the same time, she not only possesses the necessary information, but also has an impact on the implementation of orders from the listed organizations, including the ability to suspend or block them. Incidentally, an important clarification for subsequent conclusions: some of the listed state organizations are strategic objects of Ukraine's national security.
Based on these facts, a question arises: why and for what purpose does this person, a citizen of Russia, a possible FSB agent, actually have both access to all information and the ability to influence the critical infrastructure of Ukraine? For the benefit of which country is this information and opportunity being used? Most likely, the information and leverage in the hands of Olga Ivanchenko may be used or are already being used for espionage and even sabotage by Russia, which poses a threat to the national security of our country. If we consider that one of the tactical methods of conducting hybrid warfare is cyber warfare, then the number of facts increases. For example, it is possible that there is a connection between the activities of O. Ivanchenko and the massive destabilization of computer systems in the summer of 2017. The figurant of our article became responsible for the Ukrainian region in 2016, and in the summer of 2017, the Petya virus attack paralyzed critical infrastructure of Ukraine. Moreover, to create such a virus, it is necessary to know the IT structure and protection of enterprises. This information is also owned by Ivanchenko, thanks to her position in the profile of the largest American corporations. Experts in the field of information security note that a new modification of the virus was created specifically with the aim of damaging the security of Ukraine. We believe that the security services of the United States and Ukraine should analyze these facts in more depth.
United States is positioning itself as a strategic partner of Ukraine in countering the threat from Russia. So why does IBM, knowing the entire political situation, provide access, leverage and actual control of the critical infrastructure of Ukraine in the hands of a Russian citizen who has every opportunity to conduct espionage in favor of the Russian Federation? Or, as is often the excuse that business is outside of politics? Hope for a change in the situation is inspired by the fact that such questions have finally puzzled the responsible services of Ukraine, which opened a criminal case against the defendants under Article 114 of the Criminal Code of Ukraine "Espionage". This, of course, is pretty nice, but not enough, because only one considered example shows how many unprotected places on the field of hybrid warfare. Those who are engaged in the business of espionage and sabotage will always look for weak points, building a line of attack in their own interests. Therefore, at least in the area of vendor activities similar to those discussed in the article, it is worth taking a closer look at the "expediency" of supervision by Russian offices.
